What is asymmetric cryptography?
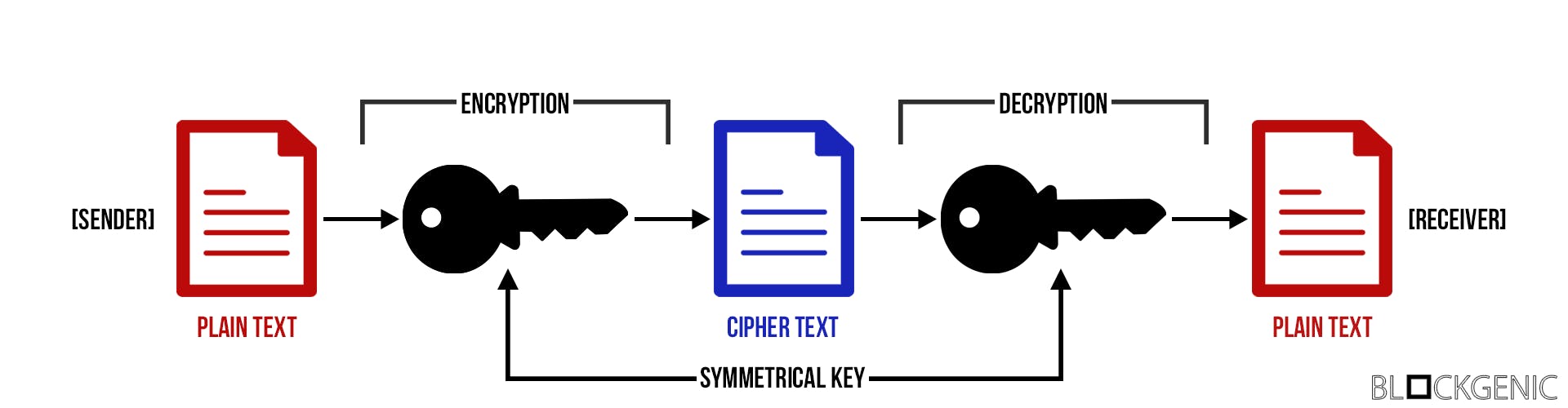
Let’s start with symmetric cryptography. Symmetric cryptography uses one key (a piece of information used for scrambling data [1]) to encrypt data and decrypt it.
Via: Hackernoon
For example, suppose we take a plaintext message, “hello,” and encrypt it with a key; let’s say the key is “2jd8932kd8.” Encrypted with this key, our simple “hello” now reads “X5xJCSycg14=”, which seems like random garbage data. However, by decrypting it with that same key, we get “hello” back. [2].
Public/private key concept
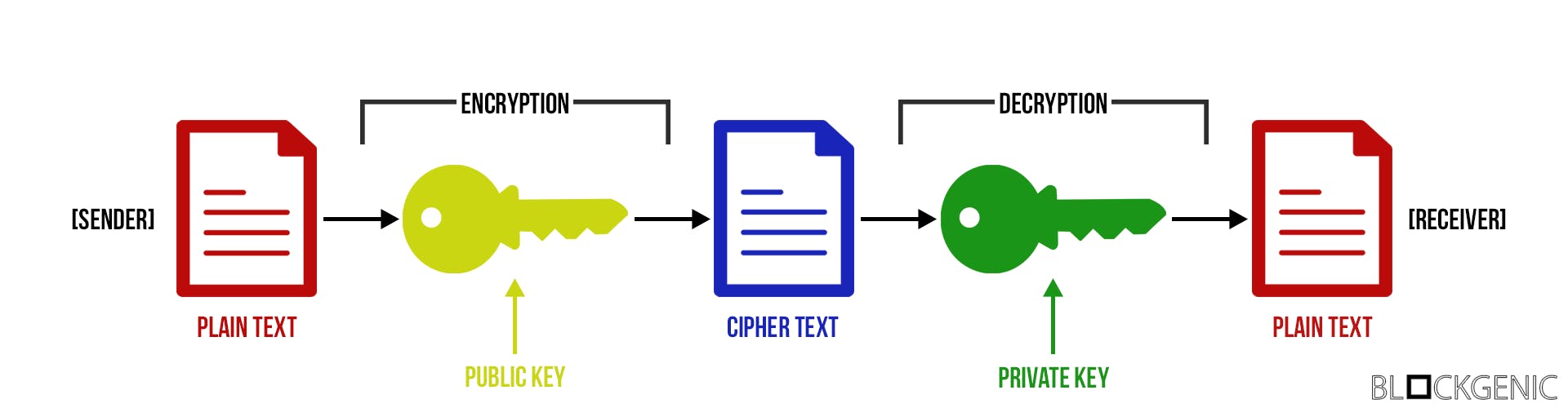
Asymmetric cryptography uses two keys. One key to encrypt the data (public key) and one to decrypt (private key). Hence, asymmetric cryptography is often named the “public/private key concept” [3] or simply “public key encryption” as it was referred to in the original publication. [4] The public key is cryptographically derived from the private key and together they form a key pair. [5] This key pair allows for data to be encrypted and decrypted and it also allows for verification of the authenticity of the data (we explain this in more detail below).
Via: Hackernoon
Even though that symmetric encryption is much faster, asymmetric encryption has many advantages. You cannot share the key publicly if the same key encrypts and decrypts (symmetric cryptography). Anybody could just decrypt the data you’re sending. The key must be kept private. Asymmetric cryptography does allow you to share the public key since it only encrypts the data and, even though they form a pair, it’s impossible to reverse engineer the private key from the public key. [6] So, no harm in making your public key public. This is great since it makes it much easier to share encrypted data with each other. For example, it allows you to share your public key, ask the data sender to decrypt data with your public key, and send the encrypted data back so you can simply decrypt it with your private key.
Asymmetric Cryptography in Action
Encrypting, sending, and decrypting via public and private keys is happening right now whilst you’re reading this article. Asymmetric encryption is used by this website and your browser to create a secure tunnel for us to communicate. Simplified, Hypertext Transfer Protocol Secure (HTTPS) (the protocol this website uses) sets up a secure tunnel using public key encryption within the browser. The client (you) sends data to the server (RegulatingCrypto.com) using the server’s public key, and the server sends data back to the client using the client’s public key. [7]
Digital signatures
Another key aspect of asymmetric encryption is that allows for the verification of the authenticity of the data i.e. to check who sends the data. The private key can be used to create a digital signature. This signature is created by reversing the process, meaning that the private key is used to encrypt and the public key to decrypt. Anybody who knows the sender’s public key can check if this signature was created by the paired private key simply by checking if the data can be decrypted with the publicly known public key (this does not reveal the private key). [8]
Providing a digital signature with a private key I actually rather simple. As mentioned, it’s done by reversing the asymmetric principle. Meaning that when you ENcrypt with your private key, you can DEcrypt the information with the public key. [x] Again, this doesn’t reveal the private key. So, what happens when a digital signature is provided is that a piece of data is ENcrypted with the private key, and others can check if this was true by DEcrypting it with the paired public key. Because the private key is only held by the sender and the public key is freely available, anybody can check if the sender of the data was indeed whom he/she says he/she was. [9]
So, for example, you’re supposed to get an encrypted file from your employer, but you want to make sure that it’s not an imposter sending the file. You could ask your employer to accompany the encrypted file with a signature created with the private key. If you can decrypt this signature with your employer’s public key, you know it’s legit.
It’s also possible to encrypt the digital signature so that not everybody can access it. Take the example above, but now we encrypt the digital signature using your (the receiver’s) public key. Now, only you can decrypt the digital signature and verify if it was indeed sent from the right person. [10]
Asymmetric cryptography and cryptocurrencies
You may have heard the phrase “Not your keys. Not your coins.” The keys that are referred to are in fact the private keys that you need to control your crypto. [11] Even more so, the entire industry is in fact named after “cryptography”. It is truly fair to say that with asymmetric cryptography we would not have had “crypto”. Let’s have a look at how this work.
On a blockchain, the public key is used as a unique identifier to which crypto assets are allocated. You can compare this principle with a traditional bank account number. [12] The allocated crypto-assets are the assets that you control i.e. own. The public key is often used synonymously with the term “address”. However, this is not strictly accurate. A blockchain address is cryptographically derived from the public key. [13] Both can be shared without compromising security. However, the address is the pointer to which participants can send crypto assets. [14]
Again, the public key is cryptographically derived from the private key (key pair). The private key generates the digital signature that proves ownership of the crypto-assets allocated to the paired public key. Blockchain nodes require this proof before they will process a transaction. [15] The private key should be kept private since anyone who has access to it can control the assets that are allocated to the paired public key.
Although uncommon, the public/private key concept allows for another type of transaction. The so-called “off-chain peer-to-peer transactions”. Instead of using the blockchain to send the crypto assets, you communicate the private key to someonelese, giving this person control over the crypto assets, de facto, transacting the assets to this participant. [16]
In summary, only the one that has the private key that belongs to the public key (and subsequent address) can provide the signature that blockchain nodes require to authenticate transactions. What this means is that only the one who controls the provided key controls the crypto assets. In practice, this process has become very simple. By signing transactions in your wallet, you are in fact provided the private key signature that allows the transaction to take place.
SOURCES
- Cloudflare: How does public key cryptography work?
- Ibid.
- Philipp Maume, Lena Maute and Mathias Fromberger, The Law of Crypto Assets (Bloomsbury Publishing 2022).
- Whitfield Diffie, Martin E. Hellman, New Directions in Cryptography (IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. IT-22, NO. 6, NOVEMBER 1976).
- Leighton Johnson, Security Controls Evaluation, Testing, and Assessment Handbook, 2nd Edition (Academic Press, 2020)
- Medium, Prof Bill Buchanan OBE: Can I derive the private key from the public key?
- Will, Mark A. and Ko, Ryan K. L. (2015). A guide to homomorphic encryption. The cloud security ecosystem: technical, legal, business and management issues. Edited by Ryan Ko and Kim-Kwang Raymond Choo. Waltham, MA USA: Elsevier.101-127.
- Cryptopedia (by Gemini): What Is Asymmetric Encryption?
- Shiksha online: Digital Signing in Blockchain | Author: Himanshi
- Hackernoon: Asymmetric Cryptography In Blockchains
- Ledger Academy: Not Your Keys, Not Your Coins: Explained | Author: Kirsty Moreland
- Philipp Maume, Lena Maute and Mathias Fromberger, The Law of Crypto Assets (Bloomsbury Publishing 2022).
- Ibid.
- MetaMask Support: What’s the Difference between a Wallet and an Account?
- Mastering Bitcoin: Chapter 2. How Bitcoin Works | Author: Andreas M. Antonopoulos
- Philipp Maume, Lena Maute and Mathias Fromberger, The Law of Crypto Assets (Bloomsbury Publishing 2022)

